Archive for 2016
Photoshop
Source click here
A PhD student at the University of Michigan that Thomas Knoll, in 1987 wrote a program on a Macintosh Plus to display grayscale images on a monochrome display. Together with his brother John Knoll who are also employees of Industrial Light & Magic, turn it into an image editor program. In 1988 the two sisters with the name change ImagePro. After that year, Thomas renamed his program into Photoshop and work in the short term with the scanner's manufacturer Barneyscan to distribute copies of the program with a slide scanner; "A total of about 200 copies of Photoshop has been sent".
During that time, John traveled to Silicon Valley in California and gave a demonstration of the program to engineers at Apple Computer Inc. and Russell Brown, art director at Adobe. The second demonstration was successful, and Adobe decided to purchase the license to distribute in September 1988. While John worked on plug-ins in California, Thomas remained in Ann Arbor writing program code. Photoshop 1.0 was released in 1990 for Macintosh.
Source click here
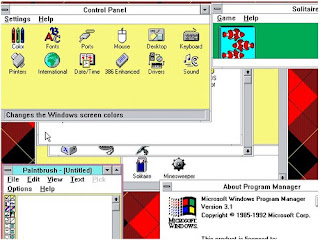
Microsoft Windows eventually achieve significant success when stepping version 3.0 which was released in 1990. In addition to offering increased capabilities to Windows applications, Windows 3.0 is also able to allow users to run multiple MS-DOS applications simultaneously (multitasking), because in this version has introduced virtual memory. This version is precisely what makes the IBM PC and compatibles serious challenger to the Apple Macintosh. This is due to improved performance graphics processing at the time (with the graphics card Video Graphics Array (VGA)), and also protected mode / 386 Enhanced mode that allows Windows applications to use more memory in a way that is much easier compared to what offered by MS-DOS.
Windows 3.0 can run in three modes, namely real mode, standard mode, and 386 Enhanced mode, and is compatible with Intel family of processors from Intel 8086/8088, 80286, to 80386 Windows 3.0 will try to detect which mode will used, although the user can force Windows to work in a certain mode using certain switches when running
win / r: force Windows to run in real mode
win / s: forcing Windows to run in standard mode
win / 3: forcing Windows to run in 386 Enhanced mode.
Version 3.0 is also the first version of Windows that runs in protected mode, although the 386 enhanced mode kernel is an enhanced version of the protected mode kernel in Windows / 386.
Because of the backward compatibility feature, Windows 3.0 applications must be compiled using 16-bit environment, so that did not use the capabilities of the Intel 80386 microprocessor, which is actually a 32-bit processor.
Windows 3.0 also comes in a version of "multimedia", called Windows 3.0 with Multimedia Extensions 1.0, which was released a few months later. This version is bundled with the existence of "multimedia upgrade kits", consisting of a CD-ROM drive and a sound card, like Creative Labs Sound Blaster Pro. This version is the pioneer of all the multimedia features present in later versions of Windows, such as Windows 3.1 and Windows for Workgroups, and become part of the Microsoft Multimedia PC specification.
The features mentioned above and support the application software market growing 3.0 makes Windows very successful in the market. Noted, in the two years prior to the release version of Windows 3.1, Windows 3.0 sold 10 million copies. Finally, Windows 3.0 was a major source of income of Microsoft, and Microsoft did make some revisions to the original plan.
The benefits of the Internet for daily life
- Internet as a source of information on any subject would be very helpful people's lives. For those who work in education, the field of literacy, or the arts, can find a variety of information from internet.Misalnya, if there is a teacher or professor who will give the subject matter and want to find more information, they can use the internet. Not only in terms of employment, anyone can find information on just about anything, for example, to find articles about disease information, information entertainment venues, etc.
- The existence of the Internet can facilitate or expedite a job. For example, there is a data from one office to be delivered to another office, this submission can use the media electronic mail (email) that would use the internet.
- In terms of relationships, the internet also has a very large role. Many forums and social networks today that can help anyone to add the association. It is also one of the benefits of the Internet for the public. The benefits of social networking is also not just add to the association, but also strengthen the friendship and make our practice to socialize better.
- The advantages of this type of business is you do not need to bother renting land / shop to sell. You just have to prepare the goods for sale, promote it, and then just wait for the buyer to contact Anda.Anda can sell just about anything over the Internet, ranging from fashion, food, services, or even sell the house.
- Therein lies the benefit of social networking on the Internet. You can use any social networking to promote, or even create a personal site that contains your efforts.
Those are some benefits of the Internet for the public. Internet simplifies life, both in terms of employment, socialization, even in terms of business.
Windows 2.1x
Furthermore, two new versions were released, namely Windows / 286 2.1 and Windows / 386 2.1. As with previous versions of Windows, Windows / 286 uses real-mode memory model, but was the first version to support the High Memory Area (HMA). Windows / 386 2.1 has a kernel running in protected mode with emulation Expanded Memory Specification (EMS) standard Lotus-Intel-Microsoft (LIM), the predecessor specifications Extended Memory Specification (XMS) which would finally change the topology of computing at the IBM PC. All Windows and DOS-based application when it was run in real mode, running over the protected mode kernel by using the virtual 8086 mode, which is a new feature which is owned by Intel 80386 2:03 Version 3.0 and later versions getting demands from Apple because the version 2.1 this has the appearance of a window in cascade mode (overlap), in addition to several features of the Apple Macintosh operating system that is "emulated" by Windows, is the main problem to see / look and feel. Judge William Schwarzer ended up canceling all 189 charges, except the nine charges filed by Apple against Microsoft on January 5, 1989.
Windows 2.x
Microsoft Windows eventually obtained a significant increase when Aldus PageMaker appeared in versions for Windows, which previously could only run on the Macintosh. Some computer historians date this, the emergence of a significant application that behavior other than by Microsoft as the early success of Windows. Windows version 2.0x using real-mode memory model, which is only able to access the memory to 1 megabyte. In such configurations, Windows can run applications more multitasking, sort DESQview, which runs in protected mode offered by the Intel 80286.
Windows 1.0
The first version of Microsoft Windows, called Windows 1.0, released on 20 November 1985. This version has many shortcomings in some functionality, making it less popular in the market. At first Windows version 1.0 is going to be named by the Interface Manager, but Rowland Hanson, the head of marketing at Microsoft Corporation, Microsoft assured officials that the name "Windows" will be "lure" customers. Windows 1.0 is not a complete operating system, but only extending the capabilities of MS-DOS to a graphical interface enhancements. In addition, Windows 1.0 also has the same problems and weaknesses that are owned by MS-DOS.
Furthermore, Apple is demanding Microsoft makes Microsoft is limiting his ability. For example, the windows in Windows 1.0 can only be displayed on the screen in "tile" only, so that the window can not overwrite each other. In addition, there is no such place that is used to save a file before it is deleted (Recycle Bin), because Apple believes that they have the rights to that paradigm. Microsoft would then throw the limitation of Windows by signing a license agreement with Apple.
Continuation of Windows 1.0 click here
The first version of Microsoft Windows, called Windows 1.0, released on 20 November 1985. This version has many shortcomings in some functionality, making it less popular in the market. At first Windows version 1.0 is going to be named by the Interface Manager, but Rowland Hanson, the head of marketing at Microsoft Corporation, Microsoft assured officials that the name "Windows" will be "lure" customers. Windows 1.0 is not a complete operating system, but only extending the capabilities of MS-DOS to a graphical interface enhancements. In addition, Windows 1.0 also has the same problems and weaknesses that are owned by MS-DOS.
Furthermore, Apple is demanding Microsoft makes Microsoft is limiting his ability. For example, the windows in Windows 1.0 can only be displayed on the screen in "tile" only, so that the window can not overwrite each other. In addition, there is no such place that is used to save a file before it is deleted (Recycle Bin), because Apple believes that they have the rights to that paradigm. Microsoft would then throw the limitation of Windows by signing a license agreement with Apple.
Continuation of Windows 1.0 click here
What's cybercrime
Cyber Crime is a new form of crime using the internet as a medium for committing crime ith the advent of the internet era. Every criminal activities committed on the internet or through the Internet, commonly referred to as Internet crime.
Types of cyber crime and violations are very diverse as a result of the application of technology. Cyber crime can be wiretapping and misuse of the information or data in electronic form and transferred electronically, theft of electronic data, pornography, abuse of a child as an object against the judiciary, fraud memalui internet, gambling diinternet, vandalism website, in addition to the heaping system through a virus, Trojan horse , signal grounding and others.
Who cybercrimes?
We need to know the perpetrators of cybercrime are those who have high expertise in computer science, perpetrators of cybercrime is generally controlled algorithms and computer programming fatherly create a script / code malware, they can analyze the workings of computer systems and networks, and is able to find loopholes pasa system will then use the weakness to be entered so that crimes such as theft of data can be successfully carried out.
Types of Cybercrime
There are several types of crimes on cyber crime can be classified based on the activities done as described below are summarized from various sources.
- unauthorized Aces => Is a crime that occurs when someone enters or infiltrate into a computer network system illegally, without permission, or without the knowledge of the owner of the computer network system is entered. Examples of these crimes are Probing and port.
- illegal Contents => A crime that is done by entering data or information into the Internet about something improper, unethical, and can be regarded as unlawful or disturb the public order, for example, is the spread of pornography or untrue reports.
- The spread of the virus intentionally => Spread of the virus is generally performed by using an email. Often people are exposed to the virus e-mail system is not aware of this. The virus is then transmitted to another place via email.
- Cyber Espionage, Sabotage, and Extortion => Cyber Espionage is a crime by way of utilizing the Internet to conduct espionage against other parties, by entering into the target computer network system. Sabotage and Extortion is the type of crime committed by creating a disturbance, destruction or the destruction of the data, computer programs or computer network system connected to the Internet.
- Carding => Carding is a crime that is made to steal credit card numbers belonging to others and used in commercial transactions on the Internet.
- Hacking and Cracker => The term hacker refers to someone who has a great interest in learning the details of computer systems and how to improve capabilities. Cracking activity on the Internet has a very wide scope, ranging from hijacking an account belonging to someone else, piracy websites, probing, spread the virus, to incapacitate the target. Last actions called DoS (Denial of Service). Dos attack is an attack aimed at paralyzing the target (hangs, crashes) therefore can not provide the service.
- Cybersquatting and typosquatting => Cybersquatting is a crime committed by registering domain names the company of others and then trying to sell it to the company with a more expensive price. The typosquatting is a crime to make a play domain is a domain that is similar to the domain name of another person.
- Cyber Terrorism => Measures cybercrime including cyber terrorism if it threatens the government or citizens, including cracking to the government or military.
Understanding of the motherboard itself that the circuit board where a variety of interconnected electronic components such as PC or Macintosh and commonly abbreviated to mobo said. Another understanding of the motherboard or in other words mainboard is the main form of pcb board that has a bios chip (driver program), lines and connectors as connecting each access device.
AT baby / AT
Motherboard AT type is the format used in the 386 and 486 first computer. then the format is replaced by the ATX format, which form the formar better air circulation than before making it easier to access the computer components.
ATX
Type of ATX motherboard can be upgraded to AT baby. It was intended to increase the convenience to you. Types This motherboard is designed to plug in peripherals as easy as possible (for example, IDE connectors are located on the side of the disc). This is the type of motherboard standard ATX, Micro ATX, Flex-ATX and mini-ATX.
BTX
BTX Motherboard type is intended to support the type of Intel that is designed to improve the setting of components, so as to optimize air circulation, acoustics, and heat control. The connectors in this motherboard installed in parallel to the direction in which air flows. BTX power cable is the same as ATX power supplies.
ITX
The motherboard is a master board in which a computer device can be installed in it. Starting from a memory, slots, processor, and many others. A motherboard is as important as a processor on the computer. If a faulty motherboard function will cause the performance of a computer so it does not become the maximum. So choosing a good motherboard that can greatly affect a performance of the computer itself. Spend a little more would be better than buying a motherboard with a low price but easily damaged, and you should also adjust the motherboard with additional devices to the computer, the device or the components are compatible and can be installed in socket located on the motherboard.
Internet is an acronym meaning networkingyang interconnected computer networks that are connected between the computer with other computers that form a network of computers around the world, so that they can interact, communicate, share information or exchange data.
Physically, the Internet can be described as webs that resemble spider webs surrounding the earth are connected through the points (nodes). Nodes can be computers and equipment (peripheral) others.
INTERNET The term comes from the Latin "inter", which means "between". In verbatim INTERNET means between or connective tissue. That's the function, INTERNET linking various networks that do not depend on each other in such a way, so that they can communicate. What system is used at each network is not a problem, whether DOS or UNIX system.
While the local network typically consists of a type of computer (eg, DOS or UNIX), INTERNET overcome differences on various operating systems by using the "language" the same by all networks in data transmission. Basically this is what causes the magnitude of the dimensions of INTERNET.
Thus, the definition INTERNET is the "network of networks", by creating the possibility of cross-network communications all over the world without depending on the type of computer.
so the internet is the relationship between different types of computers and networks in the world a different operating system or application in which these relationships utilizing advances in communication media (telephone and satellite) that uses standard protocols to communicate the protocol TCP / IP.
You know who invented 4g?Scientists from Indonesia deserves thumbs up. He is known as the inventor of the technology based 4G Network OFDM (Orthogonal Frequency Division Multiplexing). Khoirul Professor Anwar was born on August 22, 1978 in Kediri, East Java. he is the son of the couple (deceased) Sudjianto with Siti PATMI a farmer in Kediri.His father died of illness when he was graduated from elementary 1990. Khoirul father died of illness, when she graduated from elementary school in 1990, her mother, and then try hard to send him, although both parents no elementary school. Since childhood, Khoirul live in poverty. But there was just a way for him to continue studying. For example, when continued high school in Kediri, suddenly there are people offering free boarding for him. Then he went to college at the Bandung Institute of Technology Department of Electrical Engineering graduated cum laude in 2000.
Then he won a scholarship to continue S2 from Panasonic at the Nara Institute of Science and Technology (NAIST) Japan and graduated in 2005 and then later he won a scholarship to continue studying S3 from the Japanese company campus same Nara Institute of Science and Technology (NAIST ) Japan. Khoirul Anwar later married with Sri Yayu Indriyani and blessed with three sons, Khoirul stayed in Nomi, Ishikawa, not far from his workplace. Despite a brilliant achievement in Japan, but Khoirul save the desire to return to Indonesia one day.
Inspired Dragon Ball - Maybe it was the fate of the scientists, when they put his theory, often considered insane. It also experienced Khoirul. Some technology experts consider it 'misguided' as he explained his theory in 2005 in Hokkaido, Japan. "When I explain, people thought I was crazy. The technology at the time was not yet over, "recalls Khoirul laughing. But the men who had lived in Japan for more than 12 years was admitted indifferent and did not surrender to prove his theory.
Interestingly, the discovery of 4G technology it says was inspired by the cartoon series Dragon Ball. Yes, the professor is not always serious struggle with books and research. Secretly she was a fan of the cartoon with the hero named Goku. "When Goku uses the forces of nature that are combined into a fireball genki dama, resulting in tremendous power. That I apply mathematical formulas. In the 4G technology, attract the energy around it.
Thanks to the invention, high-speed internet can now be felt by many people. While it might be a misnomer, in Indonesia when the new arrival of 4G LTE, many other countries have felt the benefits since a few years ago. Though the technology is actually the son of the inventor of Indonesia.
Despite doing well in Japan, Khoirul save the desire to return to Indonesia. Spirit of learning that never dies making continued to hone skills. This brilliant figure wants to return to Indonesia when it has become one of the leading figures in the field of telecommunications.
Microprocessor is a typical chiri fourth-generation computers that are thousands of IC compaction into a chip. Because the shapes are getting smaller and the increasing capabilities and offer prices are also increasingly murah.Microprocessor the beginning of the birth of the personal computer. In 1971, Intel Corp later developed the first microprocessor serie 4004.
Examples of this generation is the Apple I Computer developed by Steve Wozniak and Steve Jobs by entering a computer microprocessor on a circuit board. In addition, later appeared TRS Model 80 with a Motorola 68000 processor type and Zilog Z-80 uses 64KB of RAM standard.
Apple II-e computers that use the processor type and Ram 6502R by 64 Kb, is also one PCs very popular at that time. Operating systems used are: CP / M 8 Bit. These computers are very popular in the early 80s.
IBM Personal Computer began issuing in about 1981, using MS-DOS Operating System 16 Bit. Due to the price offered is not much different from the other computer, in addition to the technology is much better as well as big names from IBM itself, then in a very short time the computer is becoming very popular.
Source:

In this third-generation technology Integrated Circuit (IC) is the central feature because it began to be used on a computer device to the current generation. IC component hybrid or solid form (SLT) and monolithyc (MST). SLT is a transistor and a diode placed separately in one place while the MST is an element of transistors, diodes, and resistors are put together in a single chip. MST more kesil but upon ability to have greater than SLT.
IC was first created by Texas istruments and Fairchild Semiconductor in 1959 which contains only six transistors. Can we compare the current processor that we use already has millions, tens, hundreds of millions of transistors, has even designed processors with billions of transistors. A remarkable development in a period of less than half a century.
The characteristics of third generation computers are:
- Because using the IC performance computers become faster and more accurate. The speed is nearly 10,000 times faster than the first generation computers.
- Improvement of the software.
- Larger memory capacity, and can store hundreds of thousands of characters (previously only tens of thousands).
- Using a magnetic disc storage media outside (external disk) the nature of the data random access (random access) with a large capacity (millions of characters).
- More efficient use of electricity.
- The ability to do multiprocessing and multitasking.
- Have used the visual display terminal and can make a sound
- The price is getting cheaper.
- The ability to communicate with other computers.

IBM S / 360, UNIVAC 1108, UNIVAC 9000, Burroughts 5700, 6700, 7700, NCR Century, GE 600, CDC 3000, 6000, and 7000, the PDP-8 and PDP-11 (the manufacturer is Digital Equipment Corporation) is an example -contoh third generation computers.
Source:
:The second generation is characterized by the following characteristics
- Use of technology in the form of transistor and diode circuit to replace vacuum tubes.
- Already using high-level programming language operations such as FORTRAN and COBOL.
- he capacity of the main memory is developed from Magnetic Core Storage.
- Using the external storage in the form of Magnetic Tape and Magnetic Disk.
- Ability to process real time and real-sharing.
- Physical size has been smaller than the first generation.
- The operation is faster, ie millions of operations per second.
- The need for less electrical power.
- he orientation program is not only focused on business applications, but also application engineering.
UNIVAC III
Compared premises tube, transistor technology is much more efficient as a switch and can be scaled down to a microscopic scale. In 2001, Intel researchers have introduced silicon smallest and fastest in the world, with a size of 20 nanometers ata comparable to a billionth of a meter, which will be used on a processor with a speed of 20 GHz (Giga Hertz). This era also marks the beginning of the minicomputer which is the second largest in the family computer. The price is cheaper than the first generation. DEC PDP-8 minicomputer was first created in 1964 for commercial data processing.
Other types of computers that appear on this generation diantaranta UNIVAC III, UNIVAC SS80, SS90, and in 1107, IBM 7070, 7080, 1400, and 1600.
Computer History Generation 3
Computer History Generation 4
Computer History Generation 3
Computer History Generation 4
source :
In mid 1950 UNIVAC made progress in several aspects of advanced programming, so it is the first general purpose computer that is designed to use both numbers and letters, and using magnetic tape as a medium for input and output. This is said to be the birth of the computer industry is dominated by IBM and Sperry. UNIVAC computer was first used for the purposes of calculating the census in the US in 1951, and operated until 1963.
Computer History Generation 2
Types of Motherboard
Computer History Generation 2
Types of Motherboard
Computers are tools used to process the data according to the commands that have been formulated. Computer word originally used to describe people who perform arithmetic calculations, with or without tools, but the meaning of the word is then transferred to the machine itself. Originally, the processing of information is almost exclusively related to arithmetical problems, but modern computers are used for many tasks unrelated to mathematics.
Broadly, the computer can be defined as an electronic device that consists of several components, which can cooperate between the components with one another to produce an information based programs and data. The computer components are included: Screen Monitor, CPU, Keyboard, Mouse and Printer (as a complement). Without a computer printer can still do its job as a data processor, but the extent of the monitor screen is not visible in print form (paper).